Explain Different Kinds of Online Threats Class 10
Information security threats are a problem for many corporations and individuals. An indirect threat tends to be vague unclear and ambiguous.

7 Types Of Cyber Security Threats
A hybrid cloud is a heterogeneous distributed system formed by combining facilities of public cloud and private cloud.

. Threats can be classified into four different categories. Dependency on computers for spellings would probably deteriorate their knowledge of the English language. The malware will steal valuable data or crash the system.
Drive-by Attack A website is loaded with a malware and when a visitor happens to come across such a website their device is infected with the malware. Maharana Pratap- Download PDF Here Aspirants can find complete information about upcoming Government Exams through the linked article. Up to 20 cash back Unsafe surfing can also lead to other threatsfrom embarrassing personal comments or images that once online are nearly impossible to erase to getting mixed up with people youd rather have had nothing to do with.
Mobile Network Security Threats. Viruses worms Trojans and spam are ubiquitous but they are just the tip of the iceberg. Different kinds of online threats.
Anything that one downloads from the internet can have hidden malware inside. 1 Threats 11 Malicious software 12 Denial-of-service attacks 13 Phishing 14 Application vulnerabilities 2 Countermeasures 21 Network layer security 22 Internet Protocol Security IPsec 23 Threat modeling 24 Multi-factor authentication 25 Security token 26 Electronic mail security 27 Firewalls 28 Browser choice 3 Protections. And you need both in life.
Network-based threats are especially common and risky because cybercriminals can steal unencrypted data while people use public WiFi networks. Physical threats to mobile devices most commonly refer to the loss or theft of a device. New technology is being released every day.
Malware is usually picked up from the internet or through ones email. Cyber criminals are getting smarter every day and are constantly using a variety of techniques both new zero-day as well as variations on old exploits. You need the security of insurance.
A Trojan horse is malware that carries out malicious operations under the appearance of a desired operation such as playing an online game. When you drive your car to work when you visit a new country when you ride your bike to a nearby shop when theres a new bug going around in town. Here public clouds are needed.
Internet shorthand acronyms emoticons and playful spelling used in student assignments. Here are some of the most common online threats to children to help you ensure yours stay safe. Phishing attacks are social engineering attacks and they can have a great range of targets depending on the attacker.
A major drawback of private deployments is the inability to scale on-demand and efficiently address peak loads. For this reason they are also called heterogeneous clouds. Cybercriminals are carefully discovering new ways to tap the most sensitive networks in the world.
HackingComputer Intrusion includes Phishing RansomwareMalware and Skimming. The plan the intended victim the motivation and other aspects of the threat are masked or equivocal. Short for malicious software malware comes in several forms and can cause serious damage to a computer or corporate network.
Trojan horse. Up to 20 cash back What are the different types of phishing attacks. Learn about 10 common security threats you.
Other common information security threats include privilege escalation spyware adware rootkits botnets and logic bombs. Risk is everywhere. Though the list of potential threats is extensive below youll see the most common security threats you should look out for.
These browser-based threats include a range of malicious software programs that are designed to infect victims computers. If you allow your children to spend considerable time surfing the web its important to know what threats they face. Trojan horses spyware adware ransomware phishing viruses worms rootkits and browser hijackers are all types of malware.
A direct threat identifies a specific target and is delivered in a straightforward clear and explicit manner. Technology with Weak Security. Here are the Top 10 Internet safety rules to follow to help you avoid getting into trouble online and offline.
Children are among the most active internet users and are unfortunately subject to a number of threats. Direct indirect veiled conditional. A Trojan horse varies from a virus because the Trojan binds itself to non-executable files such as image files audio files.
Chat sessions while multitasking online proved to be a distraction. Up to 20 cash back Web-based threats or online threats are malware programs that can target you when youre using the Internet. Protecting business data is a growing challenge but awareness is the first step.
The main tool behind such browser-based infections is the exploit pack which gives cybercriminals a route. THE 12 TYPES OF CYBER CRIME. There are literally a dozen ways in which a cybercrime can be perpretrated and you need to know what they are.
Mobile Device Security Threats. There are two broad types of insurance. Phishing can also be a targeted attack focused on a specific individual.
Here are the top 10 threats to information security today. They could be generic scam emails looking for anyone with a PayPal account. Threats were relatively few as perceived by the students.

8 Most Common Cybersecurity Threats Types Of Cyber Attacks Cybersecurity For Beginners Edureka Youtube

Cost Reduction Opportunities Across Value Chain Powerpoint Sales And Marketing Online Business Opportunities Reduction

Ikea Presentation Mar 5125 Business Theories Swot Analysis Pestle Analysis

Top 10 Common Network Security Threats Explained

Infographic How To Prevent Malware Malware Security Solutions Security Patches

Round And About Productivity Work Life Balance Realities Threats And Motivators Productivity Infographic Work Life Balance Infographic

10 Common Internet Security Threats And How To Avoid Them

Explain Different Kind Of Online Threats Class 10 Answer Fast Don T Spam Brainly In

10 Types Of Identity Theft You Should Know About Info Savvy Identity Theft Identity Competitive Intelligence

Conversation Corner At The Market English Conversation Learning Conversational English English Lessons

Detecting A Phishing Email Cyber Security Cyber Security Awareness Cyber Awareness

Cyber Security Infographic Template Cybersecurity Infographic Cyber Security Free Infographic Templates

25 Best Cyber Security Associate Degree Online Programs 2020 Guide Online Programs Career Development Cyber Security

Cyber Espionage A Digital License To Kill Infographic James Bond Infographic Computer Security Infographic
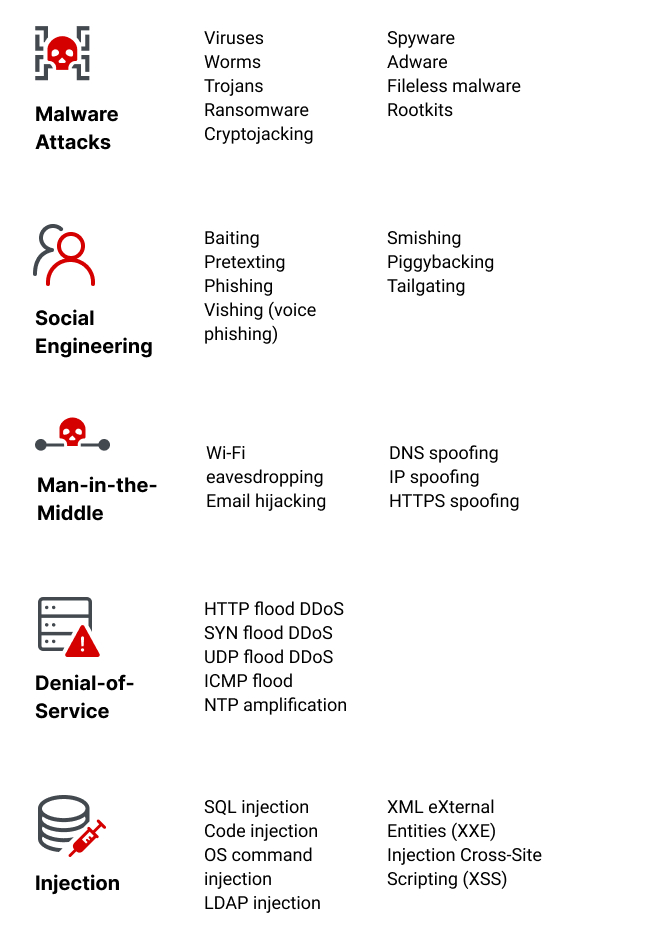
Cyber Security Threats Types Sources Imperva
Types Of Cyber Threat In 2021 It Governance Uk

Security Awareness Poster Used To Educate People On How To Recognize Fake Emails And Ph Cyber Security Education Information Technology Humor Computer Security

Accurate Timekeeping Has Become A Critical Component Of Modern Software Deployments Whether It S Makin Software Deployment Scripting Language Javascript Class

Online Threats 101 Infographic Computer Security Cyber Security Awareness Computer
Comments
Post a Comment